Hardware problems are quite difficult to tackle, worse if under Windows. There was once when installing a software, I accidentally inserted the Audio hardware diskette. Thinking it was harmless, I went on, thinking I can always "undo" everything again. How wrong was I. The next moment I restarted Windows, I got the blue screen of death. Yeah, Windows is very nasty when it comes to hardware.
Find The Culprit
Always calm down. Try to solve the problem yourself before resolving to formatting or sending to your computer dealer. First, know what's happening and the cause of it. In my case, the installation must have overwrite my old setting and replaced the wrong file. There must be a reason why Windows is acting improperly.
Logging Back On
First, try to log back on. If you can't log into Windows, don't panic. Restart the computer. When the text "Starting Windows 98..." appears, press F8. A menu will appear. Choose "Safe Mode" to continue. Safe mode will take some time to load. When you are in Windows, go to Control Panel, System. Click on the Device Manager tab. Find the faulty hardware driver and delete it. Open autoexec.bat and config.sys (both are hidden files in your root directory) with notepad. If the hardware is a CD-ROM or sound card, it will probably write add some lines. Check whether there are backup file (autoexec.bak, autoexec.b~k e.g.) since most installation will back up the 2 important files. If there is, simply replace them with the backup files. If there isn't, put "REM " in front of every line that loads the hardware.
Repairing
When you restart, your computer is probably ok, since you have deleted all instances of the hardware drivers. But the hardware isn't functioning. re-install the hardware drivers, restart and you're done! If the problem persists, your probably have a system conflict go to the next page for more.
Thursday, December 27, 2007
How to change the windows default identity?
In windows XP, you can change the windows default identity (Computer Manufacturer Logo and other information's) and share your own private identity there. First you right click on My Computer then click on Properties, here may be you will see computer manufacture logo or empty area. So add your own logo there to make your computer more private.
Follow the given steps to change the system default Properties identity:
First click on Start button and type notepad in Run option then press Enter.
Now type the following text in notepad.
[General]
Manufacturer="thecomputer-zone.blogspot.com"
Model="All about computer and phone"
[Support Information]
Line1="We offer various topics including computer tips and tricks, troubleshooting"
Line2="Visit daily for new topics "thecomputer-zone.blogspot.com"
There are some standard keywords, for example Manufacturer, Model, Line 1, Line 2; you can not change these keywords. Now save this notepad file in c:/windows/system32 folder with file name, OEMINFO.INI.
Now choose your favorite picture to set as logo, using any picture editor resize the picture size approx. 150X150 pixels then save it in c:/windows/system32 folder with file name OEMLOGO.BMP.
Now close the all files and restart your computer after any changes to go into effect. To verify these changes, right click on My Computer and open Properties.
Under General tab, verify the system properties with new settings.
Now click on Support Information for more detail.
Follow the given steps to change the system default Properties identity:
First click on Start button and type notepad in Run option then press Enter.
Now type the following text in notepad.
[General]
Manufacturer="thecomputer-zone.blogspot.com"
Model="All about computer and phone"
[Support Information]
Line1="We offer various topics including computer tips and tricks, troubleshooting"
Line2="Visit daily for new topics "thecomputer-zone.blogspot.com"
There are some standard keywords, for example Manufacturer, Model, Line 1, Line 2; you can not change these keywords. Now save this notepad file in c:/windows/system32 folder with file name, OEMINFO.INI.
Now choose your favorite picture to set as logo, using any picture editor resize the picture size approx. 150X150 pixels then save it in c:/windows/system32 folder with file name OEMLOGO.BMP.
Now close the all files and restart your computer after any changes to go into effect. To verify these changes, right click on My Computer and open Properties.
Under General tab, verify the system properties with new settings.
Now click on Support Information for more detail.
Tuesday, December 25, 2007
How to protect your document against unwanted changes?
You can protect your document by enabling the option "Protect Document". You can easily track any changes that were made in your document by any unauthorized users. The system shows that text in red color, if any one makes changes.
To enable the Protect document option, follow the given steps:
First open any word file then click on Tools in menu bar.
In Tools menu bar, click on "Protect Document". A window will open with many options to protect your important document for
Comments options allow the user to put in comment for that document.
Forms option allows the user to edit the forms in the document.
You can choose any one option to restrict the user. You can use the "Password (optional)" option to lock or unlock the document.
To protect your document, type a new password here then word will open "Confirm Password" dialog box for the confirmation of passwords. The maximum length of password is 15 characters.
Press Ok button to finish the process.
To enable the Protect document option, follow the given steps:
First open any word file then click on Tools in menu bar.
In Tools menu bar, click on "Protect Document". A window will open with many options to protect your important document for
- Tracked changes
- Comments
- Forms
Comments options allow the user to put in comment for that document.
Forms option allows the user to edit the forms in the document.
You can choose any one option to restrict the user. You can use the "Password (optional)" option to lock or unlock the document.
To protect your document, type a new password here then word will open "Confirm Password" dialog box for the confirmation of passwords. The maximum length of password is 15 characters.
Press Ok button to finish the process.
Sunday, December 23, 2007
How to hide computer drives to secure data?
This tip is very useful for home users, particularly for those who wants to hide/secure there important data from other users. You can hide any specific local drive or all drives (physical and removable) of the system and network drives also. By disabling the display of drives, you can safe your personal data from non-technical users on a single computer.
Follow the given steps to change the system drives registry value:
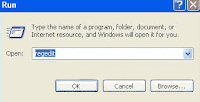
Here locate the location to:
· HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion \Policies\Explorer
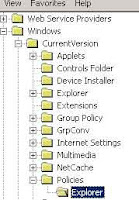
· Here in right side panel, right click to create a new DWORD value with name NoDrives (it is case sensitive), then assign number to its value data box.
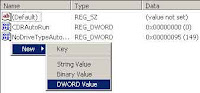
· Now if you want to hide all system drives then modify value data to 3FFFFFF.
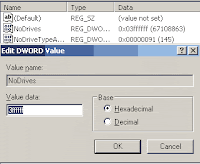
· For specific drive use values (For example, for A, B, C, D, E, F, G, H drives, the values are 1, 2, 4, 8, 16, 32, 64, and 128 respectively). · In this case we are trying to hide F drive, so we modify the value data box to 32.
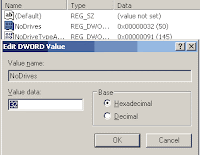
· Now close the registry editor and restart your computer after any changes to go into effect. · But next time, if you want to unhide this drive then simply change the value data box or delete the DWORD item. Again close the registry editor and restart your computer after any changes to go into effect.
Follow the given steps to change the system drives registry value:
- To use this feature, you will need to be logged into your computer with administrative rights.
- Click Start button and type regedit in Run option then press Enter for next.

Here locate the location to:
· HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion \Policies\Explorer

· Here in right side panel, right click to create a new DWORD value with name NoDrives (it is case sensitive), then assign number to its value data box.

· Now if you want to hide all system drives then modify value data to 3FFFFFF.

· For specific drive use values (For example, for A, B, C, D, E, F, G, H drives, the values are 1, 2, 4, 8, 16, 32, 64, and 128 respectively). · In this case we are trying to hide F drive, so we modify the value data box to 32.

· Now close the registry editor and restart your computer after any changes to go into effect. · But next time, if you want to unhide this drive then simply change the value data box or delete the DWORD item. Again close the registry editor and restart your computer after any changes to go into effect.
Tuesday, December 18, 2007
Cognos puts BI on Nokia and Windows Mobile phones
(IDG News Service) -- Cognos Inc. said today that its Cognos 8 Go Mobile business intelligence (BI) software now supports Windows Mobile 6 smart phones, as well as Nokia Corp. E-series and N-series devices running S60 Third Edition on the Symbian operating system.
The software works with Cognos' core BI system and can automatically reformat reports for various types of devices.
The Ottawa-based company had already developed support for Research In Motion Ltd.'s BlackBerry smart phones.
Cognos' move to support more mobile platforms is logical, according to David O'Connell, an analyst at Nucleus Research Inc. in Wellesley, Mass.
"They're going mobile. They've been doing it for a while," O'Connell said. "Basically, the more platforms you can put BI on, the more people you have adopting it, so there's more ROI [return on investment]."
Anastasia Valentine, product manager at Cognos, said the company made the new clients in response to market interest. Customer interest in Windows Mobile 6 centered in the U.S. and the Asian-Pacific region, while European customers wanted support for Nokia devices, she said.
While the new products are fine-tuned for each platform, they are identical in features to the BlackBerry client, according to Valentine.
Support for one of this year's hottest mobile devices, Apple Inc.'s iPhone, isn't yet on Cognos' docket.
Despite the iPhone's explosive popularity, its immediate value to enterprises has been questioned. Forrester Research Inc. recently issued a report listing reasons why IT departments shouldn't support it, at least for now. Those warnings include the device's lack of support for push e-mail and its cost, Forrester said.
Valentine said Cognos isn't seeing much customer demand for iPhone support, adding that the company is also keeping an eye on Google Inc.'s Android mobile development platform.
A "starter pack" for Cognos' mobile BI software, which includes a server-based license, licenses for 25 users and one year of support, costs $31,000, Valentine said.
The software works with Cognos' core BI system and can automatically reformat reports for various types of devices.
The Ottawa-based company had already developed support for Research In Motion Ltd.'s BlackBerry smart phones.
Cognos' move to support more mobile platforms is logical, according to David O'Connell, an analyst at Nucleus Research Inc. in Wellesley, Mass.
"They're going mobile. They've been doing it for a while," O'Connell said. "Basically, the more platforms you can put BI on, the more people you have adopting it, so there's more ROI [return on investment]."
Anastasia Valentine, product manager at Cognos, said the company made the new clients in response to market interest. Customer interest in Windows Mobile 6 centered in the U.S. and the Asian-Pacific region, while European customers wanted support for Nokia devices, she said.
While the new products are fine-tuned for each platform, they are identical in features to the BlackBerry client, according to Valentine.
Support for one of this year's hottest mobile devices, Apple Inc.'s iPhone, isn't yet on Cognos' docket.
Despite the iPhone's explosive popularity, its immediate value to enterprises has been questioned. Forrester Research Inc. recently issued a report listing reasons why IT departments shouldn't support it, at least for now. Those warnings include the device's lack of support for push e-mail and its cost, Forrester said.
Valentine said Cognos isn't seeing much customer demand for iPhone support, adding that the company is also keeping an eye on Google Inc.'s Android mobile development platform.
A "starter pack" for Cognos' mobile BI software, which includes a server-based license, licenses for 25 users and one year of support, costs $31,000, Valentine said.
Monday, December 17, 2007
Personal and Family uses of VOIP
Today, VOIP is not an unknown word for the people. People around the globe are looking towards this option of communication. No, doubt, today it’s being used broad only for the business purpose, but the time is not farther when it will become first choice of the people, all over the globe. Actually, VOIP is the short form of Voice over Internet Protocol, which allows people to communicate on phone through internet.
VOIP technology has totally changed the communication world. Some of the people think it is good for the large businesses, which need several long distance calls regularly, but the fact, probably they don’t know that, not only small businesses are getting the advantage of VOIP, but it has also much benefit for those, who want to use it personally and for family; and those, who know, are not having information enough about what they have to do. Here it is in brief, what and how VOIP provides:
o No matter, where you are in whole world; if you have VOIP technology, you are always close to your family. VOIP will never let you feel that you are living apart. Whenever, you wish you can have a chat as long as you want, because VOIP is an internet service, which requires no extra charge. Once you have brought just you need to pay your monthly internet fees. With other old phone services, you are not free; the huge bills will accost you to do so.
o If your children or friends are out of country because of any reason, either it is study or business purpose, you don’t need to miss them, when and how long you wish, they will be in your touch.
o It may be much helpful in distance learning. Whether it is meeting, or any other situation, which needs you to be gathered, now can handle without being together. VOIP has a great facility, which lets you talk with many people together.
o Except these, what facilities usually people expect to have with old phone service at additional charges, are given as common with VOIP.
These are some points which indicate the importance of VOIP and tell you how and how much you can save. Now here is what you are required to do to get the best VOIP service:
o First step is to buy a high speed internet in order to get fast and fine service. Normal connection is unable to run this.
o Second expense, you have to make to purchase a gateway or, if you want to use your current phone, adaptor; which makes link between internet and your phone.
o Last and common step, you know very well, is only to shop around. This will give you best VOIP service at reasonable price.
VOIP is a very modern telecommunication tool, which is brought the people very close to each other. You can talk to the person face to face (through video phones), who is thousands of miles far from you. So, it’s not bad idea to buy VOIP for using personally.
VOIP technology has totally changed the communication world. Some of the people think it is good for the large businesses, which need several long distance calls regularly, but the fact, probably they don’t know that, not only small businesses are getting the advantage of VOIP, but it has also much benefit for those, who want to use it personally and for family; and those, who know, are not having information enough about what they have to do. Here it is in brief, what and how VOIP provides:
o No matter, where you are in whole world; if you have VOIP technology, you are always close to your family. VOIP will never let you feel that you are living apart. Whenever, you wish you can have a chat as long as you want, because VOIP is an internet service, which requires no extra charge. Once you have brought just you need to pay your monthly internet fees. With other old phone services, you are not free; the huge bills will accost you to do so.
o If your children or friends are out of country because of any reason, either it is study or business purpose, you don’t need to miss them, when and how long you wish, they will be in your touch.
o It may be much helpful in distance learning. Whether it is meeting, or any other situation, which needs you to be gathered, now can handle without being together. VOIP has a great facility, which lets you talk with many people together.
o Except these, what facilities usually people expect to have with old phone service at additional charges, are given as common with VOIP.
These are some points which indicate the importance of VOIP and tell you how and how much you can save. Now here is what you are required to do to get the best VOIP service:
o First step is to buy a high speed internet in order to get fast and fine service. Normal connection is unable to run this.
o Second expense, you have to make to purchase a gateway or, if you want to use your current phone, adaptor; which makes link between internet and your phone.
o Last and common step, you know very well, is only to shop around. This will give you best VOIP service at reasonable price.
VOIP is a very modern telecommunication tool, which is brought the people very close to each other. You can talk to the person face to face (through video phones), who is thousands of miles far from you. So, it’s not bad idea to buy VOIP for using personally.
Sunday, December 16, 2007
[Photoshop] Make Glossy Text
In this Adobe Photoshop video tutorial I will show you how easy it is to make a web 2.0 graphic element. It tutorial was actually improvised, I opened Photoshop and started drawing and adding effects. Its not the most challenging and advanced effect, but I think it sums up a lot of issues concerning how to make a simple web 2.0 graphic element.
Here is the final result.

Start by making a rectangle selection over the stage as shown below, then fill it with a random color (it will be changed later).

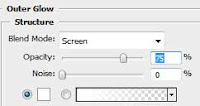
Now in the layers panel, double click the new shape layer to get to the layers style panel and give it styles as shown below.
Now put in your text on top of the rectangle shape in a separate layer, I choose to put in two X's (Don't ask why).
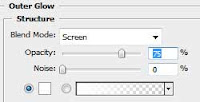
For the shape of text you put in, double click the layer to get to the styles panel and give it settings as shown below.
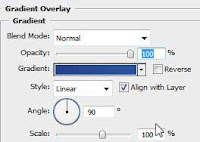
Make a new layer above all other layers and name it reflection, then hold down ctrl key and click the first rectangle shape layer to load the shape selection. Now with the selection tool subtract from selection as shown below.

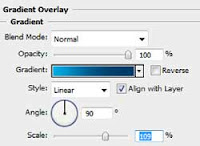
Now make a gradient going from white to transparent color and apply it to the selection so you get a result like below.

Here is the final result.

Start by making a rectangle selection over the stage as shown below, then fill it with a random color (it will be changed later).

Now in the layers panel, double click the new shape layer to get to the layers style panel and give it styles as shown below.



Now put in your text on top of the rectangle shape in a separate layer, I choose to put in two X's (Don't ask why).
For the shape of text you put in, double click the layer to get to the styles panel and give it settings as shown below.


Make a new layer above all other layers and name it reflection, then hold down ctrl key and click the first rectangle shape layer to load the shape selection. Now with the selection tool subtract from selection as shown below.

Now make a gradient going from white to transparent color and apply it to the selection so you get a result like below.

Thursday, December 13, 2007
[Flash] Animated Roll On/Off Menu
- The first step is to create an image to use for the menu. This image can be made in Photoshop

- Open flash and import the menu_img button. (File > Import > Import to library) and select the image.
- In the library you will find the image you just imported. Drag the image to the stage. On the TIMELINE, rename the layer for the button you're going to create (for instance, if you're going to make this a home page buttons, rename the layer "home"). Repeat until you have all the buttons you want on the stage and on their own layer.

- Once you have the buttons named and ready, its time to convert them to movie clips. Select the first image and convert it into a movie clip (Modify > Convert to symbol > Movie clip) and name each movie clip.

- Once you have converted the images to movie clips, we must give each clip and INSTANCE NAME. To do this, find the instance name box just below the stage to the left. Make sure you give each clip a different instance name (in this example, we named the home button "home_mc").
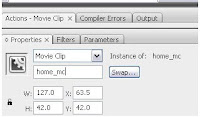
- Once all your buttons have been given distinct instance names, its time to get busy creating the fun stuff. Double clicking the "home" button will let you work inside the home movie clip. Once inside the movie clip, the button image will be on layer 1. Rename this layer "image" and create 3 new layers above the "image" layer. Starting with the top layer, rename them "actions", "over", and "text".

- First we will add the moving white box. Working on the "over" layer, use the Rectangle tool to create a white box with the same dimensions as the button image. Move the box up so that it is off the stage and immediately above the menu image. Now select the image and convert this box to a GRAPHIC and rename it "white_over_gf". With the white box graphic selected, change the opacity of it by going down to the COLOR drop down and select ALPHA and change the alpha % to 35%.


- Next we will add the text to the button. On the TEXT layer, type in whatever you wish for your button. Then convert this newly created text to a MOVIE CLIP.

- Next we need to add KEYFRAMES to our button timeline. To place a keyframe, select the frame you wish to place it and either INSERT > TIMELINE > KEYFRAME. Add keyframes to the frame 1 and 7 on the ACTIONS, OVER, and TEXT layers and on the 12th frame of the TEXT and OVER layers. Next, add a regular frame on the 12th frame of the IMAGE and ACTIONS layer. (to add a regular frame, highlight the frame you wish and Insert > Timeline > Frame).

- Now we are going to add some STOP actions to the 1st and 7th frame of the ACTIONS layer. On the 1st keyframe in the ACTIONS layer, open the actions window (Windows > Actions). Once open, type "stop();" Repeat this action for both frames. Once you have finished, there will be a small "a" in both keyframes.

- Now we are going to add some motion to the over box. Select the keyframe on frame 7 of the OVER layer. Using the cursor, move the white box down so that it matches up perfect over the menu image. Next, select the keyframe on frame 12 of the OVER layer, and cursor that white box so that it is directly below the menu image. Select the space between frame 1 and 7 on the OVER layer. In the properties panel bottom, select MOTION from the drop down box next to TWEEN. An arrow should appear in the timeline between the keyframes. Repeat this for the space between keyframes 7 and 12 on the OVER layer.

- Almost done! Now go back to the main timeline by clicking the "Scene 1" icon. Create a new layer above all the buttons and name this layer "overs". On this new layer, use the RECTANGLE tool to create a rectangle that matches the dimensions of the menu_img.jpg graphic. Convert this new rectangle to a BUTTON.

- Set the ALPHA of the button to 0% so that it is transparent. Repeat this until all the movie clips have buttons over them.

- Now, with the transparent button selected, open the Actions window and add the following actionscript to the button:

- That's it! Enjoy!
Wednesday, December 12, 2007
Viruses - What They Are And One Reason Why People Make Them
Over recent years, computers have become synonymous with viruses and viruses don't show any signs of disappearing any time soon. In recent news, LiveScience.com reported that "Before the month is even done, April has set a record for virus e-mails."1 In the past, we would be comfortable in telling new computer users not to worry about viruses and that catching a computer virus is rare. Today, that would be some of the worst advice we could give anyone. As reported in countless news reports, computer viruses are rampant and they're extremely worrisome. This article will describe what viruses are and then point you in the direction of some rather unique protection and prevention.
In short, a computer virus is a software program designed to destroy or steal data. It attacks computers via distribution - often unknowingly - through email attachments, software downloads, and even some types of advanced web scripting. Viruses that destroy data are known as Trojan horses, viruses that explode their attacks are called bombs, and viruses that duplicate themselves are called worms. Some viruses are a combination of each, however they can be further identified according to where they're located on a computer.
A virus originating from the boot sector of a computer is a boot-sector virus and this nasty devil does its dirty work the moment a computer is turned on. A virus that attaches itself to (infects) other programs is a file virus and activates the moment that an infected program starts. File viruses may also be referred to as parasitic viruses, however should a virus work from both the boot-sector and from an infected program, the virus is then known as a multipartite virus.
Why viruses exist remains a mystery, however we had privy access to the mind behind a virus programmer who explained his motivation behind his destructive inclinations. Apparently, this person had a deep grudge against a popular online service which shall remain unnamed. In this hacker's mind, the online service failed to do a quality job in protecting children from online smut and as retaliation, he created and distributed a virus to as many file libraries of this service as he could. His intentions were to disable the computers of the online service's users so much that they wouldn't be able to connect for days. In his mind, the loss of connection meant loss of revenue for the online service.
Although the malicious code that this person generated may have worked for a small percentage of users, sufficed to say, the online service continued on and still exists today. Despite his motivation or intention, his efforts were null.
We wouldn't be surprised to learn if other motivations behind spreading viruses were similar to this person's, but that doesn't justify the damage that viruses do. Innocent people become pawns for the evil plans of others who've convinced themselves they're doing the "right" thing.
To protect a computer from getting a virus, or clean a virus from a computer system once infected requires the use of an antivirus utility. But may be something else we can do. Perhaps we could make an effort to educate the people who want put viruses into the public about ways to display dissatisfaction with a service or product that don't involve harming innocent parties. In doing so, we just might reduce the number of virus news stories and protect our own investments at the same time.
In short, a computer virus is a software program designed to destroy or steal data. It attacks computers via distribution - often unknowingly - through email attachments, software downloads, and even some types of advanced web scripting. Viruses that destroy data are known as Trojan horses, viruses that explode their attacks are called bombs, and viruses that duplicate themselves are called worms. Some viruses are a combination of each, however they can be further identified according to where they're located on a computer.
A virus originating from the boot sector of a computer is a boot-sector virus and this nasty devil does its dirty work the moment a computer is turned on. A virus that attaches itself to (infects) other programs is a file virus and activates the moment that an infected program starts. File viruses may also be referred to as parasitic viruses, however should a virus work from both the boot-sector and from an infected program, the virus is then known as a multipartite virus.
Why viruses exist remains a mystery, however we had privy access to the mind behind a virus programmer who explained his motivation behind his destructive inclinations. Apparently, this person had a deep grudge against a popular online service which shall remain unnamed. In this hacker's mind, the online service failed to do a quality job in protecting children from online smut and as retaliation, he created and distributed a virus to as many file libraries of this service as he could. His intentions were to disable the computers of the online service's users so much that they wouldn't be able to connect for days. In his mind, the loss of connection meant loss of revenue for the online service.
Although the malicious code that this person generated may have worked for a small percentage of users, sufficed to say, the online service continued on and still exists today. Despite his motivation or intention, his efforts were null.
We wouldn't be surprised to learn if other motivations behind spreading viruses were similar to this person's, but that doesn't justify the damage that viruses do. Innocent people become pawns for the evil plans of others who've convinced themselves they're doing the "right" thing.
To protect a computer from getting a virus, or clean a virus from a computer system once infected requires the use of an antivirus utility. But may be something else we can do. Perhaps we could make an effort to educate the people who want put viruses into the public about ways to display dissatisfaction with a service or product that don't involve harming innocent parties. In doing so, we just might reduce the number of virus news stories and protect our own investments at the same time.
Integrated Services Digital Network (ISDN) Configuration
ROUTER A-CISCO
A-CISCO#configure terminal
A-CISCO (config)#isdn switch-type basic-net3
A-CISCO (config)# dialer-list 1 protocol ip permit
A-CISCO (config)#interface bri0
A-CISCO (config-if)#ip address 1.1.1.1 255.0.0.0
A-CISCO (config-if)#encapsulation ppp
A-CISCO (config-if)#dialer-group 1
A-CISCO (config-if)#dialer map ip 1.1.1.2 2451458
A-CISCO (config-if)#dialer idle-timeout 180
ROUTER B-CISCO
B-CISCO#configure terminal
B-CISCO (config)#isdn switch-type basic-net3
B-CISCO (config)# dialer-list 1 protocol ip permit
B-CISCO (config)#interface bri0
B-CISCO (config-if)#ip address 1.1.1.2 255.0.0.0
B-CISCO (config-if)#encapsulation ppp
B-CISCO (config-if)#dialer-group 1
B-CISCO (config-if)#dialer map ip 1.1.1.1 2051458
B-CISCO (config-if)#dialer idle-timeout 180
Current Configuration
!
version 12.0
service timestamps debug uptime
no service password-encryption
!
hostname A-CISCO
!
enable password cisco
!
isdn switch-type basic-net3
!
interface BRI 0
ip address 1.1.1.1 255.0.0.0
encapsulation ppp
dialer map ip 1.1.1.2 2451458
dialer group 1
dialer idle-timeout 180
!
dialer-list 1 protocol ip permit
!
line con 0
end
Current Configuration
!
version 12.0
service timestamps debug uptime
no service password-encryption
!
hostname B-CISCO
!
enable password cisco
!
isdn switch-type basic-net3
!
interface BRI 0
ip address 1.1.1.2 255.0.0.0
encapsulation ppp
dialer map ip 1.1.1.2 2051458
dialer group 1
!
dialer-list 1 protocol ip permit
!
line con 0
transport input none
line aux 0
line vty 0 4
no login
!
end
A-CISCO#configure terminal
A-CISCO (config)#isdn switch-type basic-net3
A-CISCO (config)# dialer-list 1 protocol ip permit
A-CISCO (config)#interface bri0
A-CISCO (config-if)#ip address 1.1.1.1 255.0.0.0
A-CISCO (config-if)#encapsulation ppp
A-CISCO (config-if)#dialer-group 1
A-CISCO (config-if)#dialer map ip 1.1.1.2 2451458
A-CISCO (config-if)#dialer idle-timeout 180
ROUTER B-CISCO
B-CISCO#configure terminal
B-CISCO (config)#isdn switch-type basic-net3
B-CISCO (config)# dialer-list 1 protocol ip permit
B-CISCO (config)#interface bri0
B-CISCO (config-if)#ip address 1.1.1.2 255.0.0.0
B-CISCO (config-if)#encapsulation ppp
B-CISCO (config-if)#dialer-group 1
B-CISCO (config-if)#dialer map ip 1.1.1.1 2051458
B-CISCO (config-if)#dialer idle-timeout 180
Current Configuration
!
version 12.0
service timestamps debug uptime
no service password-encryption
!
hostname A-CISCO
!
enable password cisco
!
isdn switch-type basic-net3
!
interface BRI 0
ip address 1.1.1.1 255.0.0.0
encapsulation ppp
dialer map ip 1.1.1.2 2451458
dialer group 1
dialer idle-timeout 180
!
dialer-list 1 protocol ip permit
!
line con 0
end
Current Configuration
!
version 12.0
service timestamps debug uptime
no service password-encryption
!
hostname B-CISCO
!
enable password cisco
!
isdn switch-type basic-net3
!
interface BRI 0
ip address 1.1.1.2 255.0.0.0
encapsulation ppp
dialer map ip 1.1.1.2 2051458
dialer group 1
!
dialer-list 1 protocol ip permit
!
line con 0
transport input none
line aux 0
line vty 0 4
no login
!
end
Monday, December 10, 2007
How to speed up your slow internet connection?
Today a special tip for those who are still using any slow dial-up internet connection due to unavailability of any broadband connection in their area. The Web Accelerator application designed to provide the full acceleration for your routine web sites browsing. With the help of Web Accelerator you can browse your internet 4 to 6 times faster than normal dial-up connection. Basically this services compressing the website text data, images and heavy graphics to open or download this data with high speed.
This technique is more useful for static websites and for email applications but don't accelerate with secure and downloading audio or video files. Some good web accelerator retains your system cache to reuse websites with faster speed and can also block windows pop-up. If you are using FTP sites and downloading any program using dial-up, then web accelerator is not for you. There are various web accelerator software are free available on internet, visit and download it to enjoy your connection.
This technique is more useful for static websites and for email applications but don't accelerate with secure and downloading audio or video files. Some good web accelerator retains your system cache to reuse websites with faster speed and can also block windows pop-up. If you are using FTP sites and downloading any program using dial-up, then web accelerator is not for you. There are various web accelerator software are free available on internet, visit and download it to enjoy your connection.
Friday, December 7, 2007
How to solve low memory problems?
Normally this warning message shows when you run many programs same time than the RAM installed on your computer is designed to support. Your can solve this problem by increasing the system paging file size also called as virtual memory. Using this virtual memory windows moving information to and from the paging file for fast processing. This will free up enough RAM for other programs to run properly.
To increase the system page file follow the give path:
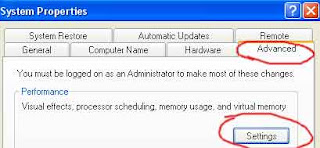
Control Panel > System > Advanced > Click on Settings (Under Performance) > Advanced > Change
Here under Drive (Volume label), you have option to select any of your hard disk drive, but the best choice is, select any drive other than C drive for virtual memory.
To increase the system page file follow the give path:

Control Panel > System > Advanced > Click on Settings (Under Performance) > Advanced > Change
Here under Drive (Volume label), you have option to select any of your hard disk drive, but the best choice is, select any drive other than C drive for virtual memory.
Thursday, December 6, 2007
How to detect viruses in a computer using multiple antivirus engines
Virus detection and its removal are made through an antivirus program which finds out viruses in a computer and then possibly removes or repairs the virus problem. But today an interesting tip, how to scan your system without any installed antivirus program. You can scan any specific file for viruses, malware, worms and trojans on your system without any preloaded antivirus protection.
VirusTotal is a free service that facilitates you for quick scan to detect viruses, malware, worms and trojans. VirusTotal will analyze your system files using multiple antivirus engines. VirusTotal is not a proper substitute of installed antivirus program, because this service works only when you will be connected to internet.
Now open the VirusTotal site to start scan process.
Now under the "Upload the file" section, click on browse button to select the virus affected file and press "Send File" button.
Here VirusTotal will takes some time to upload file (depends upon the file size and internet speed).
 Now scanning process will be started to scan affected file.
Now scanning process will be started to scan affected file.
It will again takes some time to scan affected file using latest antivirus version and gives you detailed results from each antivirus engine with statistics.
VirusTotal is a free service that facilitates you for quick scan to detect viruses, malware, worms and trojans. VirusTotal will analyze your system files using multiple antivirus engines. VirusTotal is not a proper substitute of installed antivirus program, because this service works only when you will be connected to internet.
Now open the VirusTotal site to start scan process.
Now under the "Upload the file" section, click on browse button to select the virus affected file and press "Send File" button.
Here VirusTotal will takes some time to upload file (depends upon the file size and internet speed).
 Now scanning process will be started to scan affected file.
Now scanning process will be started to scan affected file.It will again takes some time to scan affected file using latest antivirus version and gives you detailed results from each antivirus engine with statistics.
Sunday, December 2, 2007
Cell phone battery didn't kill S. Korean worker, LG says
A South Korean construction worker who was reported to have been killed by an exploding cell phone battery was actually killed in an industrial accident, South Korean news reports and cell phone maker LG Electronics Inc. said today.
The unnamed worker was found dead Wednesday with a melted cell phone in his breast pocket. Initial reports quoted police as saying they presumed the death was due to the cell phone battery exploding.The initial reports "led to the unfair assumption by the media and the general public that an LG product was somehow the cause of this tragedy. This undeservedly damaged the company's reputation for more than a day," cell phone maker LG Electronics said in a statement.
The story made headlines worldwide in part because several companies have had to recall batteries in recent years because of defects that could cause the batteries to explode and injure users. Earlier this year, the world's biggest cell phone maker, Nokia Corp., issued an advisory about faulty batteries in some of its phones. It offered to replace about 46 million Nokia-branded BL-5C batteries because they could short-circuit and overheat while recharging.
In South Korea, news media reports today said the death of the quarry worker was an industrial accident. The Chosun Ilbo and Yonhap News reported the man was hit by a co-worker driving a backhoe.
The Korea Times said the phone may have caught on fire as a result of the heavy impact with the backhoe.
The Importance Of Backup in Our Life
If you are new computer user first you should learn about the importance and need of back up. Because without backup yon can lose your data any time due to any virus, power failure and hard disk problem. This has happened to many people. In extreme cases, it has put companies out of business. Computers are becoming more and more reliable. This creates a false sense of security - we begin to think all our data are safe and secure and will never go away. It's not true - and never will be. If you don't back up your computer system regularly. Backups are really a necessity, and you are responsible for making backups of your files.
Subscribe to:
Posts (Atom)



