SEOUL -- South Korean police said what they thought had been a death caused by an exploding mobile phone was actually a ruse by a co-worker to cover up an accidental vehicular homicide.
Police and a doctor who examined the body of a 33-year-old quarry worker had said on Thursday the victim was found dead with a burning mobile phone stuck to his chest and they were looking into whether he was killed by an exploding battery.
"The co-worker confessed to us last night [Thursday] that he had actually hit him by accident and lied about the mobile phone exploding," said an official with the Cheongju Heungdeok police station, about 60 miles southeast of Seoul.
The co-worker confessed to police that he pinned the victim to a rock face while backing up a construction vehicle.
Police are investigating whether the phone caught fire because of intense pressure or if the co-worker set it ablaze, local media reported.
The victim, who was pronounced dead on arrival at a hospital, had burns on his chest, fractured ribs and internal bleeding, the doctor said.
Earlier today, police said the construction worker was killed in an industrial accident, when he was struck by a backhoe, according to South Korean news reports and cell phone maker LG Electronics.
In a statement, LG Electronics said earlier reports that the phone in the accident was made by LG "led to the unfair assumption by the media and the general public that an LG product was somehow the cause of this tragedy. This undeservedly damaged the company's reputation for more than a day," the cell phone maker said.
Friday, November 30, 2007
Sunday, November 25, 2007
How to backup of your computer installed drivers?

You can easily create the backup of your computer installed drivers (just the particular or all drivers) and use it to troubleshoot any driver problems. This backup will be very useful when you will format your computer window due to any reason. There is no need to search the drivers from internet or drivers CD, just import the driver backup and within five minute, you will complete the driver installation process. You can move this backup from one computer to other computer for installation.
To complete the all process, we will use a simple tool called drivermex. Using this tool, we can easily export the backup of any specific or all drivers and then import it for reinstallation later or elsewhere. You can free download (with free registration code) this tool for windows XP and Vista also. Download it and run the easy setup.
After Installation launch drivermex, the first screen you will get with title “Drivermex - Version” and options “Export drivers, Import drivers and Installed drivers report”. Just click on “Export Driver” option to start backup process.
Now after welcome screen, system will take few seconds to create the list of all installed drivers and then show you all installed drivers list.
Here you can select any specific device driver or click on “Select all” button to create the backup of entire installed drivers.
Press the Next button and in next screen you can select the export type (simple backup or in zip format) and then choose the backup location (always choose drive other than C drive).
Again press the Next and system will take some time (depend upon the size of your drivers) to finish exporting the selected drivers.
Click the “Open extraction folder “button to view the backup files or press Close button to finish it.
Now you can use this backup files (using import option) to restore drivers backup or move to any other computer. Copy the Following link to download it.
www.innovative-sol.com/drivermax/index.htm
To complete the all process, we will use a simple tool called drivermex. Using this tool, we can easily export the backup of any specific or all drivers and then import it for reinstallation later or elsewhere. You can free download (with free registration code) this tool for windows XP and Vista also. Download it and run the easy setup.
After Installation launch drivermex, the first screen you will get with title “Drivermex - Version” and options “Export drivers, Import drivers and Installed drivers report”. Just click on “Export Driver” option to start backup process.
Now after welcome screen, system will take few seconds to create the list of all installed drivers and then show you all installed drivers list.
Here you can select any specific device driver or click on “Select all” button to create the backup of entire installed drivers.
Press the Next button and in next screen you can select the export type (simple backup or in zip format) and then choose the backup location (always choose drive other than C drive).
Again press the Next and system will take some time (depend upon the size of your drivers) to finish exporting the selected drivers.
Click the “Open extraction folder “button to view the backup files or press Close button to finish it.
Now you can use this backup files (using import option) to restore drivers backup or move to any other computer. Copy the Following link to download it.
www.innovative-sol.com/drivermax/index.htm
Wednesday, November 21, 2007
How to change the boot Time in window XP?
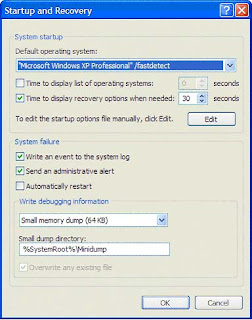 You can set the boot time in windows XP as your wish if you are install two operating systems on same computer, for example window 2000 with windows XP or more than two. Yow can do this with editing Boot.ini file. Here you can also set the sequence for operating system which operating system boot first.
You can set the boot time in windows XP as your wish if you are install two operating systems on same computer, for example window 2000 with windows XP or more than two. Yow can do this with editing Boot.ini file. Here you can also set the sequence for operating system which operating system boot first. First Right Click on My Computer option and then select its Properties. In next dialog box open Advanced tab button. Under Startup and Recovery, click on the Settings button. Use the spin box "Time to display list of operating systems" to set the number of seconds you want the system to wait before automatically starting the default operating system. Here you will set time in seconds and its range start from 0 and ends with 999 seconds.
After set the time, then click OK option to close the dialog box to save your change. The next time you restart, the new time will take effect.

New PARC software turns a cell phone into a personal assistant
Ever wish you had a personal assistant? Someone who could recommend a good restaurant when you're traveling to a new city? Someone who could give you a list of shops where you might find that perfect gift?
In a few years, that personal assistant just might be your own cell phone.
Engineers at Palo Alto Research Center Inc. (PARC) have developed software that they say can make recommendations about local restaurants, concerts, shopping areas and other activities based on the time of day, the user's physical location and the user's personal tastes. The researchers aim to let the software, called Magitti, turn a cell phone into a personal assistant of sorts.
"We're trying to make [the cell phone] more like a human," said Victoria Bellotti, a principal scientist at PARC. "Instead of just directing stuff at you, it tries to make inferences about what kind of activity you're engaged in. On a Sunday afternoon, it might suggest going to a park or a gallery. It will learn patterns based on what you tend to show an interest in. It looks at things like where you go, what recommendations you liked. It's like having a companion with you."
PARC is researching and developing the software on behalf of a Japanese company, Dai Nippon Printing Co. Bellotti said PARC already tried the software out on users in the Palo Alto, Calif., area, and it will have its first official trial run in Japan next spring. She added that it is tentatively slated for release during 2009.
Bellotti said the software focuses on five different activity modes: eating, shopping, seeing, doing and reading. The software, in essence, learns from the user. What does he like to do on Friday nights? What types of restaurants does he prefer when he's out of town? Where does he like to shop on Sundays? Magitti will offer suggestions to users based on the answers to such questions.
"It doesn't directly know anything except the time and location and how you interact with it," explained Bellotti. "It provides a list of recommendations. It will give you a wide range of what would be in a city guide. You get a big list and then you can ask to see more details. Then it can show you where these things are on a map. If it realizes you are shopping, it will offer you information to make it easier."
Bellotti said the software uses artificial intelligence algorithms that make inferences about what the user is doing by comparing the GPS location of, say a restaurant he frequents for brunch, with a database of eateries. Based on the knowledge the Magitti accumulates, recommendations will change, and hopefully become more honed, over time.
Don't like what the software is giving you for options? Say no and redirect it by doing a search for something different, she added. The software also learns by what users dismiss.
"Our hope is that over time, it will get more and more clever using your past behaviors to know you better and know your preferences better," said Bellotti. "Eventually, it will know that you will generally want a restaurant recommendation at 9 o'clock at night. It will know you want to go hear music on a Friday night. You have a routine. There are times you go to the gym. There are times you want to do something different."
In a few years, that personal assistant just might be your own cell phone.
Engineers at Palo Alto Research Center Inc. (PARC) have developed software that they say can make recommendations about local restaurants, concerts, shopping areas and other activities based on the time of day, the user's physical location and the user's personal tastes. The researchers aim to let the software, called Magitti, turn a cell phone into a personal assistant of sorts.
"We're trying to make [the cell phone] more like a human," said Victoria Bellotti, a principal scientist at PARC. "Instead of just directing stuff at you, it tries to make inferences about what kind of activity you're engaged in. On a Sunday afternoon, it might suggest going to a park or a gallery. It will learn patterns based on what you tend to show an interest in. It looks at things like where you go, what recommendations you liked. It's like having a companion with you."
PARC is researching and developing the software on behalf of a Japanese company, Dai Nippon Printing Co. Bellotti said PARC already tried the software out on users in the Palo Alto, Calif., area, and it will have its first official trial run in Japan next spring. She added that it is tentatively slated for release during 2009.
Bellotti said the software focuses on five different activity modes: eating, shopping, seeing, doing and reading. The software, in essence, learns from the user. What does he like to do on Friday nights? What types of restaurants does he prefer when he's out of town? Where does he like to shop on Sundays? Magitti will offer suggestions to users based on the answers to such questions.
"It doesn't directly know anything except the time and location and how you interact with it," explained Bellotti. "It provides a list of recommendations. It will give you a wide range of what would be in a city guide. You get a big list and then you can ask to see more details. Then it can show you where these things are on a map. If it realizes you are shopping, it will offer you information to make it easier."
Bellotti said the software uses artificial intelligence algorithms that make inferences about what the user is doing by comparing the GPS location of, say a restaurant he frequents for brunch, with a database of eateries. Based on the knowledge the Magitti accumulates, recommendations will change, and hopefully become more honed, over time.
Don't like what the software is giving you for options? Say no and redirect it by doing a search for something different, she added. The software also learns by what users dismiss.
"Our hope is that over time, it will get more and more clever using your past behaviors to know you better and know your preferences better," said Bellotti. "Eventually, it will know that you will generally want a restaurant recommendation at 9 o'clock at night. It will know you want to go hear music on a Friday night. You have a routine. There are times you go to the gym. There are times you want to do something different."
Microsoft confirms that XP contains random number generator bug
Windows XP, Microsoft Corp.'s most popular operating system, sports the same encryption flaws that Israeli researchers recently disclosed in Windows 2000, Microsoft officials confirmed late Tuesday.
The researchers, Benny Pinkas from the University of Haifa and two Hebrew University graduate students, Zvi Gutterman and Leo Dorrendorf, reverse-engineered the algorithm used by Windows 2000's pseudo-random number generator (PRNG), then used that knowledge to pick apart the operating system's encryption. Attackers could exploit a weakness in the PRNG, said Pinkas and his colleagues, to predict encryption keys that would be created in the future as well as reveal the keys that had been generated in the past.
As recently as last Friday, Microsoft hedged in answering questions about whether XP and Vista could be attacked in the same way, saying only that later versions of Windows "contain various changes and enhancements to the random number generator." Yesterday, however, Microsoft responded to further questions and acknowledged that Windows XP is vulnerable to the complex attack that Pinkas, Gutterman and Dorrendorf laid out in their paper, which was published earlier this month.
Windows Vista, Windows Server 2003 and the not-yet-released Windows Server 2008, however, apparently use a modified or different random number generator; Microsoft said they were immune to the attack strategy.
In addition, Microsoft said Windows XP Service Pack 3 (SP3), a major update expected sometime in the first half of 2008, includes fixes that address the random number generator problem.
Microsoft and Pinkas have argued over whether the flaw was a security vulnerability, with the former denying the bug met the definition and the latter claiming it is a serious problem that -- while it needs to piggyback on another, more common kind of exploit -- is far from just a theoretical threat.
Tuesday, even as it conceded that XP also had a weak PRNG, Microsoft continued to downplay the possibility of an attack. "If an attacker has already compromised a victim machine, a theoretical attack could occur on Windows XP," a company spokeswoman said in an e-mail. To exploit the PRNG's flaws, an attacker must have administrative rights to the PC, something that's easily obtained by most run-of-the-mill attacks, Pinkas noted.
Previously, Microsoft had used that prerequisite to reject any claim that Windows 2000 contained the security vulnerability, since Pinkas' proposed attack could not accomplish anything on its own. Microsoft stuck to that position with XP. "Because administrator rights are required for the attack to be successful, and by design, administrators can access all files and resources on a system, this is not inappropriate disclosure of information," the company spokeswoman added.
Newer operating systems, however, are completely in the clear. "Windows Vista, Windows Server 2008 and Windows Server 2003 SP2 are not affected by the type of attack Pinkas describes," said the spokeswoman.
Pinkas applauded Microsoft's decision to patch Windows XP. "We're happy to learn that Microsoft is acknowledging that our attack is indeed an issue, and will fix it in XP SP3."
While Microsoft said it will fix the PRNG in Windows XP, it remained mute about patching the flaw in Windows 2000. The aging operating system, which, according to a recent survey by Forrester Research Inc., still powers approximately 9% of all American and European business computers, is in the last stages of support. In that phase, dubbed "extended support," Microsoft is committed to providing only security updates free of charge.
Because the company has determined that the PRNG problem is not a security vulnerability, it is unlikely to provide a patch.
The researchers, Benny Pinkas from the University of Haifa and two Hebrew University graduate students, Zvi Gutterman and Leo Dorrendorf, reverse-engineered the algorithm used by Windows 2000's pseudo-random number generator (PRNG), then used that knowledge to pick apart the operating system's encryption. Attackers could exploit a weakness in the PRNG, said Pinkas and his colleagues, to predict encryption keys that would be created in the future as well as reveal the keys that had been generated in the past.
As recently as last Friday, Microsoft hedged in answering questions about whether XP and Vista could be attacked in the same way, saying only that later versions of Windows "contain various changes and enhancements to the random number generator." Yesterday, however, Microsoft responded to further questions and acknowledged that Windows XP is vulnerable to the complex attack that Pinkas, Gutterman and Dorrendorf laid out in their paper, which was published earlier this month.
Windows Vista, Windows Server 2003 and the not-yet-released Windows Server 2008, however, apparently use a modified or different random number generator; Microsoft said they were immune to the attack strategy.
In addition, Microsoft said Windows XP Service Pack 3 (SP3), a major update expected sometime in the first half of 2008, includes fixes that address the random number generator problem.
Microsoft and Pinkas have argued over whether the flaw was a security vulnerability, with the former denying the bug met the definition and the latter claiming it is a serious problem that -- while it needs to piggyback on another, more common kind of exploit -- is far from just a theoretical threat.
Tuesday, even as it conceded that XP also had a weak PRNG, Microsoft continued to downplay the possibility of an attack. "If an attacker has already compromised a victim machine, a theoretical attack could occur on Windows XP," a company spokeswoman said in an e-mail. To exploit the PRNG's flaws, an attacker must have administrative rights to the PC, something that's easily obtained by most run-of-the-mill attacks, Pinkas noted.
Previously, Microsoft had used that prerequisite to reject any claim that Windows 2000 contained the security vulnerability, since Pinkas' proposed attack could not accomplish anything on its own. Microsoft stuck to that position with XP. "Because administrator rights are required for the attack to be successful, and by design, administrators can access all files and resources on a system, this is not inappropriate disclosure of information," the company spokeswoman added.
Newer operating systems, however, are completely in the clear. "Windows Vista, Windows Server 2008 and Windows Server 2003 SP2 are not affected by the type of attack Pinkas describes," said the spokeswoman.
Pinkas applauded Microsoft's decision to patch Windows XP. "We're happy to learn that Microsoft is acknowledging that our attack is indeed an issue, and will fix it in XP SP3."
While Microsoft said it will fix the PRNG in Windows XP, it remained mute about patching the flaw in Windows 2000. The aging operating system, which, according to a recent survey by Forrester Research Inc., still powers approximately 9% of all American and European business computers, is in the last stages of support. In that phase, dubbed "extended support," Microsoft is committed to providing only security updates free of charge.
Because the company has determined that the PRNG problem is not a security vulnerability, it is unlikely to provide a patch.
Subscribe to:
Posts (Atom)